What is Identity and Access Management?
Identity and Access Management (IAM) is the security discipline that enables individuals to access the right resources at the right times for the right reasons. IAM addresses the mission-critical need to ensure appropriate access to resources across heterogeneous technology environments, and to meet increasingly rigorous compliance requirements. The goal of this service is to implement an IAM platform to address the university needs to manage identity and access issues for internal and external users.
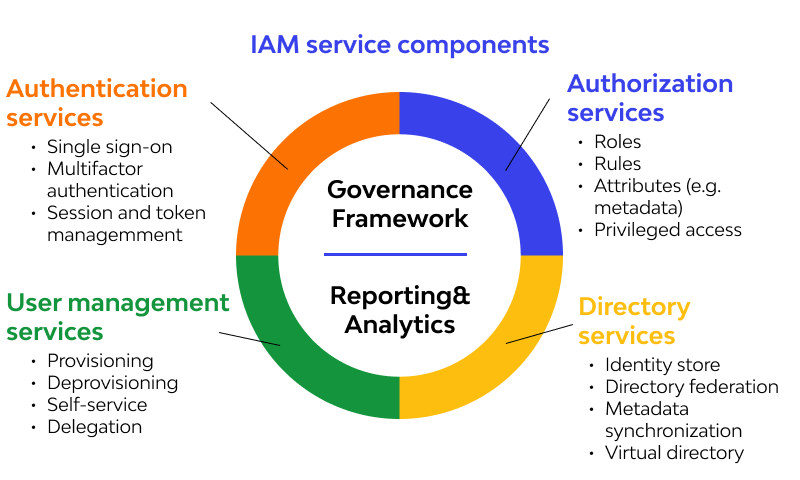
How IAM Works
There are two parts to granting secure access to an organization’s resources: Identity management and access management.
identity management
Identity management checks a login attempt against an identity management database, which is an ongoing record of everyone who should have access. This information must be constantly updated as people join or leave the organization, their roles and projects change, and the organization’s scope evolves.
Examples of the kind of information that’s stored in an identity management database include employee names, job titles, managers, direct reports, mobile phone numbers, and personal email addresses. Matching someone’s login information like their username and password with their identity in the database is called authentication.
Access management
Access management is the second half of IAM. After the IAM system has verified that the person or thing that’s attempting to access a resource matches their identity, access management keeps track of which resources the person or thing has permission to access. Most organizations grant varying levels of access to resources and data and these levels are determined by factors like job title, tenure, security clearance, and project.
Granting the correct level of access after a user’s identity is authenticated is called authorization. The goal of IAM systems is to make sure that authentication and authorization happen correctly and securely at every access attempt.
Importance and Benefits of IAM
- It helps our IT department strike the right balance between keeping important data and resources inaccessible to most but still accessible to some
- Role-Based Access Control (RBAC) is a scalable way to restrict access to only the people who need that access to perform their role. Roles can be assigned based on a fixed set of permissions or custom settings.
- IAM tools like single sign-on (SSO) and unified user profiles make it possible to grant secure access to employees across multiple channels like on-premises resources, cloud data, and third-party applications without multiple logins.
Office of Information Security
InformationSecurity@csub.edu
(661) 654-3425
Doug Cornell
Information Security Officer
dcornell@csub.edu
(661) 654-3474
Office: LIB ITV2C
Return to Information Security Home