Phishing Protection
Table of Contents
What is Phishing?
Phishing is the fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers.
It is a method of trying to gather personal information using deceptive e-mails and websites. Spear phishers distribute malware in emails or breach your account to steal personal and organization information. These emails are designed to mimic communications from trustworthy sources, aiming to deceive users into providing authentic credentials or enticing them to disclose sensitive information such as usernames, passwords, and other personal identifiers. 91% of data security breaches start with an email attack.
Malicious actors exploit this information to:
- Extract funds from victims, such as altering direct deposit details or emptying bank accounts.
- Engage in identity theft activities, including making unauthorized charges on credit cards or initiating the opening of new accounts.
- Utilize compromised email accounts to disseminate spam.
- Capitalize on obtained credentials to infiltrate other campus systems, launch attacks on external systems, pilfer University data, and undermine the campus's objectives.
Remember, CSUB will NEVER ask you for your password via email! IF IT LOOKS SUSPICIOUS, DELETE THE MESSAGE.
If you do accidentally send your CSU, Bakersfield or MyCSUB User Name and Password via email, or enter them into a suspicious website, immediately change your password on MyID or by calling the Service Center at (661) 654-4357.
Email Digests
If our email protection service does identify a viral attachment or a spam email, it will stop the email from being delivered to your Inbox. In an effort to identify and resolve false positives (that is, emails that were thought to be spam that were not), you may receive an 'email digest' twice daily. The email digest is a list of new emails blocked by the email protection server. If you identify an email that you would like released to you, please contact the Service Center by email or by phone at 661-654-HELP(4357).
How Do I Spot and Avoid Spoofed Websites?
Scams are growing in number and in sophistication. One way involves using spoofed websites – clever imitations designed to resemble legitimate businesses, including financial institutions. To spoof a website, bad actors purchase "sponsored links” to fake sites that appear at the top of search results. Their goal is to boost their site’s visibility and lure unsuspecting users into clicking on them. These deceptive sites can pose severe risks by exposing users to potential malware, identity theft, and financial loss.
Here’s what to watch for:
- URL errors and issues: Look for misspellings or unusual domain extensions. A single letter out of place might mean you’re on a fake site.
- Grammar and spelling mistakes: Legitimate sites take care to avoid errors. If you spot poor grammar, spelling, or formatting mistakes in content, that’s often your first clue it’s a fake site.
- False security notification: Once you click on a site link, you’re presented with a screen notifying you of a login issue and directing you to a hotline number. Wording on these fake sites may mention “unauthorized activity” or other details designed to trigger anxiety and panic.
- Request for personal information: legitimate companies will never ask you over the phone for your account login password. If someone is asking you for your account login password by phone, do not provide it.
- Privacy policy: Genuine sites will have a privacy policy available. If it’s missing, think twice.
How Do I Spot Phishing Emails?
Exercise caution with all requests. Ask yourself, "Is this real?" Refer to the following checklist to identify common signs of phishing messages:
- Message indicates urgent action is needed
- Message indicates negative consequences will occur if action is not taken
- Message is not expected
- Message sender is not known or a forged (spoofed) account
- Message cannot be read without opening an attachment
- Message requests sensitive information be sent
- Message directs users to "click here"
- Message uses poor grammar and/or spelling
- Sender from: name does not match message signature
- Sender email address does not match organization name
- Sender email address is not the same as the real address
- Sender name is not listed in the campus directory
Common Phishing Emails
A common tactic involves offering internship or job opportunities, often using the names of faculty members or departments and use compromised CSUB accounts to lend credibility to their messages.
Another common tactic is when attackers provide a sense of urgency in their phishing emails. They often try to imitate our CSUB IT Department and threaten account deletion or deactivation if you don't provide vital information.
Very rarely will a student/faculty/staff member have their account compromised where an online attacker was able to get into their account. They will send phishing emails from an actual CSUB email account, but be aware they are NOT legitamate offers or emails.
While many of these communications are genuine, some are not. Here are some signs to help you differentiate.
Be cautious if an email or job posting:
- Doesn't specify the company name
- Comes from an email address that doesn't match the company name (e.g., @gmail.com instead of @csub.edu)
- Lacks essential contact information for the employer, such as the sender's title, company address, and phone number
- Contains vague content, along with typos and grammatical errors
- Does not include official CSUB logos or signatures
Be wary if you are asked to:
- Pay an application fee
- Provide credit card or bank account details
- Transfer funds via payment apps (Venmo, PayPal, Cash App), wire service, courier, or other methods
- Share sensitive information via email, such as your address, birthday, gender, ID/driver's license copy, social security number, or bank account details
How Do I Report Phishing Emails?
Method 1: Email Forwarding
- If you receive an email you believe to be a phishing attempt, foward the email to InformationSecurity@csub.edu.
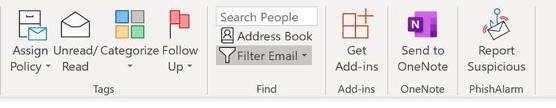
Method 2: Report Suspicious Button
- The icon that will show up in Outlook (whether you are using a Desktop or Mobile device)
looks like an envelope with a blue hook with the text "Report Suspicious" below it
as pictured below.

- In Outlook on the Desktop or from a desktop browser, the Icon appears at the far right
of the Outlook toolbar
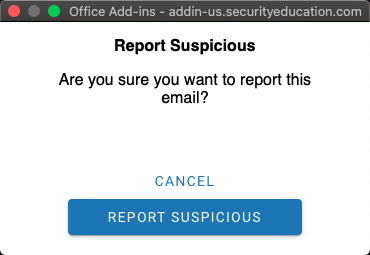
*Note: To see the Report Suspicious plug-in show up in Outlook on MacOS, navigate to Outlook > Preferences > Privacy, select "Enable optional connected experiences," then restart Outlook. - When there is an email you'd like to report, select the email and click the "Report
Suspicious" (Phish Alarm) button. A window will pop up asking you to confirm you would
like to report this email as suspicious.
This will report the email to Proofpoint and the Information Security team for review. If the email is considered malicious by Proofpoint, the quarantine process will start automatically. If the email needs further review, it will be forwarded to the Information Security team. - To report a suspicious email on a mobile client (Android or iOS), you select the three
dots ( ... ) underneath the Date/Time of the email.
On Android:
On iOS: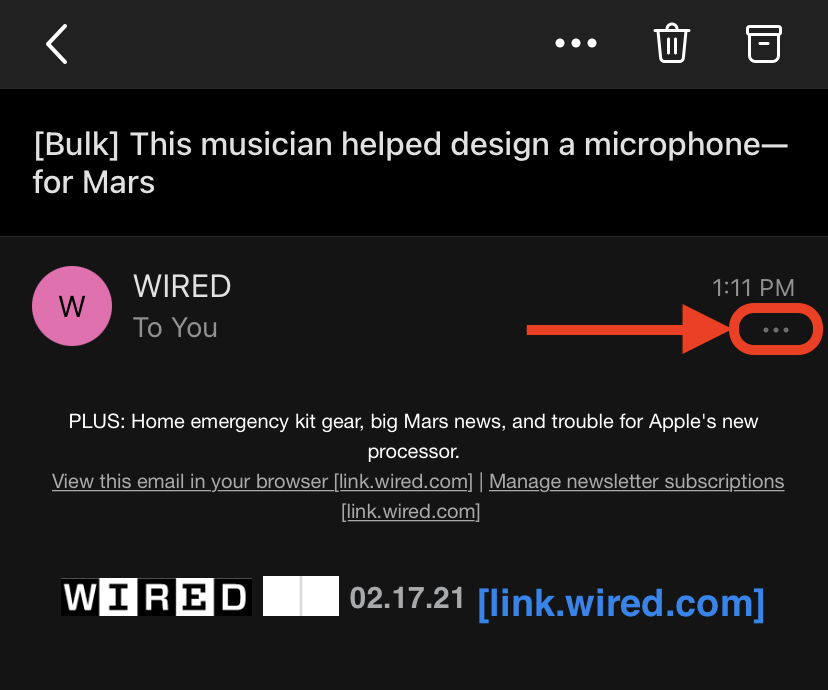
Then select the Report Suspicious button that becomes available.
On Android: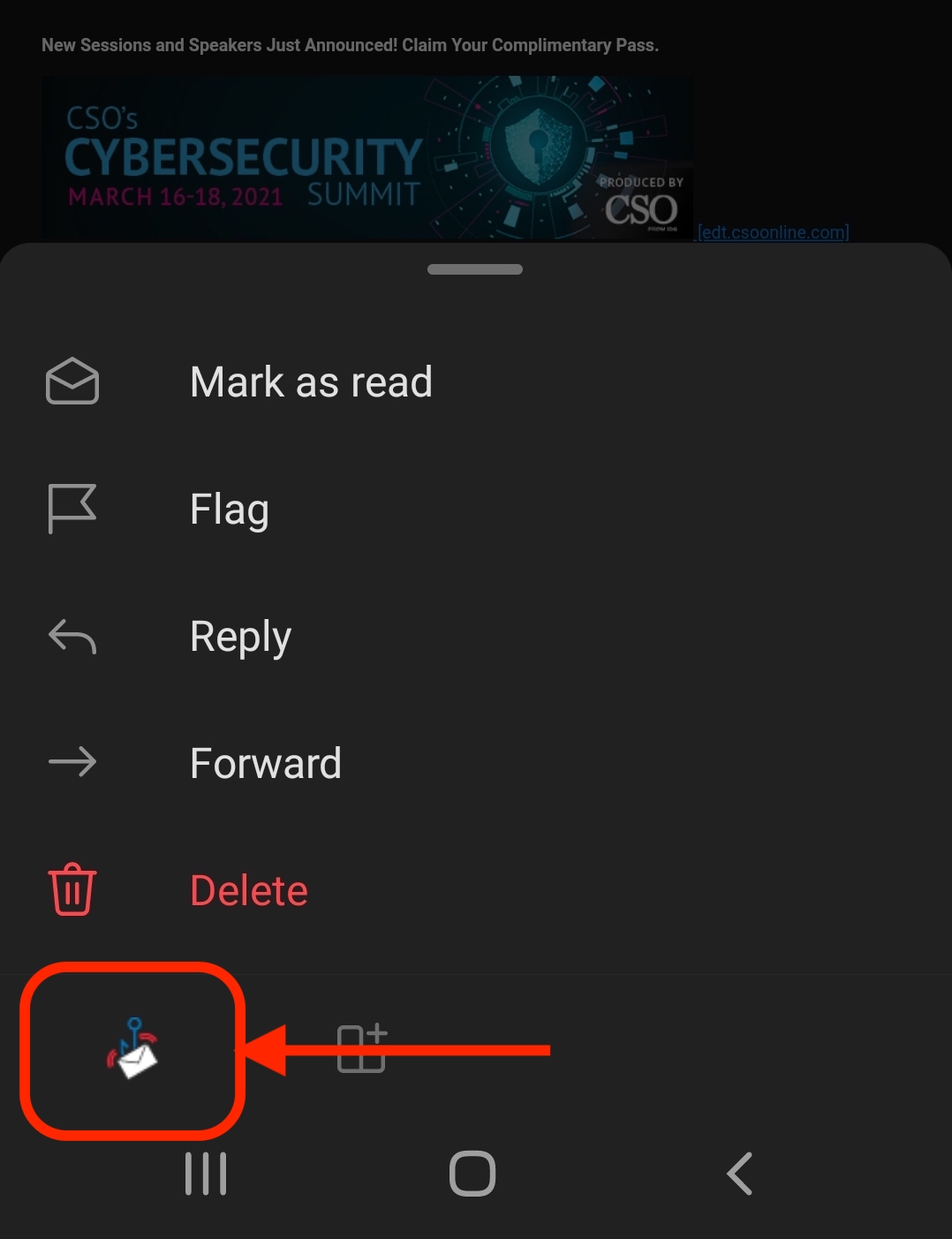
On iOS: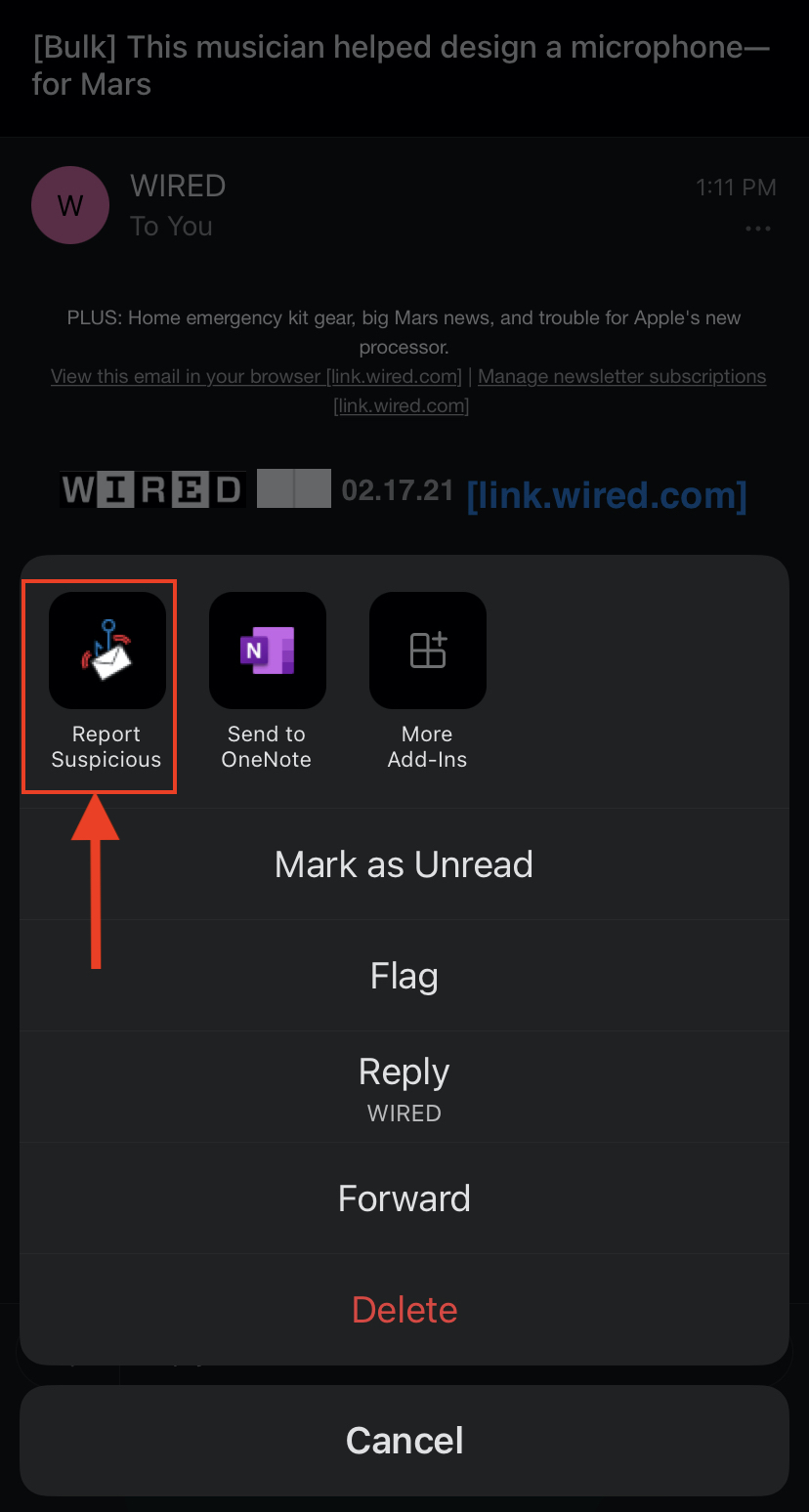
A window will pop up asking you to confirm you would like to report this email as suspicious.
Anatomy of a Phishing Email
Most phishing scams share common elements. Here are some examples of phishing attempts that could land in your email inbox. Below each example are a few key points to spot that the email is a phishing attempt.
WHO Internship UNICEF InternshipApplications are invited for the World Health
Organizations(WHO)1 Internship Program 20202.
Work hours are 4-6 hours each week and pay is
$350 / week3. It offers a wide range of oppor-
tunities for students and staff of colleges
in the USAto gain insight in the technical
and administrative programs of WHO. Prior
work experience isn’t needed. Kindly Click
Here4 to apply or forward this to any-
body that might be interested in the program.
Good luck & Best Regards.Hello,
Just to touch base with you1 and let you know
that there is a 3 month part-time job intern-
ship2 with UNICEF3. It’s a work from home job
and perfect for students and staff. Flexible
Part-Time Job, Earn up to $300 weekly4. Get
more details and apply below:
APPLY HERE WITH UNICEF INTERNSHIPS5
Regards.
2. Fake employment offer.
3. Promise of payment is often a trick.
4. Don't click! Hovering your cursor over the link will likely reveal a bogus site.
2. Fake employment offer.
3. Fraud schemes often associates with legitimate organizations.
4. Promise of payment is often a trick.
5. Don't click! Hovering your cursor over the link will likely reveal a bogus site
Financial Scam Spoofed Contact—-------- Forwarded message —--------
From: Spoofed Name<spoofedemail@bogus.edu>1
Date: Thu, Feb 13, 2020 at 12:45 PM
Subject: Re: Urgent follow up2
To: Real Person <dontbeavictim@email.edu>
Ok. I’ll be having a busy day, i need 10
pieces of Amazon card $100 face value each,
I need to get the physical card then you
scratch the card take a picture of the
card pin, attach and email it to me or
order online from the amazon store online3.
How soon can you get this done?
Regards
Spoofed Signature4—-------- Forwarded message —--------
From: CSU Bakersfield <bogusemail@csub.edu>1
Date: Wed, Mar 25, 2020 at 10:09 PM
Subject: Changes on Staff Pay and Benefits2
To:
Dear colleagues,
There is an urgent update3 about the staff
pay and benefits for the month of march4
kindly check the HR information page5 for
more detail information.
Fake Signature Block6
California State University Bakersfield
Bakersfield,
California
93311
Attachment7
2. Sense of Urgency.
3. The Scam.
4. Spoofed Signature.
2. Legitimate Subject.
3. Sense of Urgency and Account Status Threat.
4. Bad Grammar and Typos.
5. Fake URL.
6. Fake Signature Block.
7. Suspicious Attachment.
Training Resources
For additional information and training, refer to the links below:
- Take the OpenDNS Phishing Quiz
- How to spot a phishing attempt
- Watch this video to learn more about phishing scams
- Cofense anti-phishing campaign
Office of Information Security
InformationSecurity@csub.edu
(661) 654-3425
Doug Cornell
Information Security Officer
dcornell@csub.edu
(661) 654-3474
Office: LIB ITV2C